The NIS2 Directive is reshaping cybersecurity standards across the EU. It no longer affects only critical infrastructure operators - it’s expanding to a much wider range of organizations, including IT service providers as a part of supply chains, but also if they themselves are large enough.
One of the most critical areas? Endpoint management. How do we protect users’ laptops, desktops, and mobile devices - those daily tools that represent the largest attack surface?
In this blog, we’ll explore what managed service providers (MSPs) need to consider when delivering endpoint management services. The post is based on experience of Plentics on ISO 27001 and NIS2 compliance, as well as expert discussions. We’ll also include a bullet-style checklist of must-do controls to meet the NIS2 bar.
Why NIS2 Matters Now
The NIS2 Directive (EU 2022/2555) is the successor to the original NIS directive. But this time, the scope is broader - many mid-sized businesses and service providers now fall under their umbrella. It’s no longer just about state-owned entities or power plants. A large chunk of the IT sector is now legally expected to meet baseline cybersecurity standards as they are crucially integrated in the supply-chains as service providers.
Endpoints and their users are risk magnets. They move around, connect to different networks, and can easily fall into the hoxes or wrong hands. It’s only natural that new legislation puts them under a microscope.
NIS2 Accountability: From the Boardroom to the Technical Frontline
NIS2 places clear accountability on executive leadership and boards. Cybersecurity is no longer just an IT department’s responsibility - it’s a strategic obligation. Senior management must ensure that appropriate risk management, continuity planning, and technical safeguards are in place. Failure to do so can lead to personal liability for decision-makers.
The penalties are real. Non-compliance can lead to fines of up to €10 million or 2 % of global annual turnover - whichever is higher. For a publicly listed critical infrastructure operator with €500 million in revenue, that could mean a full €10 million fine - or even more. This isn’t theoretical: we’ve already seen hundreds of millions of penalties under GDPR, and regulators are expected to take a similarly strict approach under NIS2. Leadership needs to act - before the authorities do it for them.
But. There are also things that are on the responsibility of technical specialists - especially when it comes to turning strategic intent into real, enforceable security controls.
While leadership defines the objectives and ensures resources are in place, technical teams are the ones who must design, implement, and maintain the actual security posture. That includes ensuring endpoint configurations meet compliance policies, updates are deployed on time, audit logs are collected and reviewed, and incident response plans are actionable - not just theoretical. If devices are unpatched, unsecured, unconfigured or misconfigured, it's usually not because the board forgot - it’s because the technical execution didn’t follow through.
In that sense, NIS2 is a shared responsibility framework. Leadership sets the tone and direction. Technical teams deliver the operational controls. One without the other is incomplete - and regulators are likely to ask questions on both fronts.
We will now outline the items that require your attention, whether you are in a leadership role or possess technical expertise in the domain of endpoint management.
How NIS2 Affects Endpoint Management
When it comes to endpoint management, the key focus areas under NIS2 are:
- Risk management
- Incident response and recovery
- Security policies and documentation
- Technical controls and encryption
- Staff training and awareness
- Supply chain security
- Logging and auditing
For MSPs, this is about more than internal security. It’s also about how you support and secure your clients’ environments. For example, tools like Microsoft Intune and Defender play a crucial role in raising client-side compliance.
Next, we list the core actions MSPs should prioritize to meet NIS2 compliance across their own and client environments.
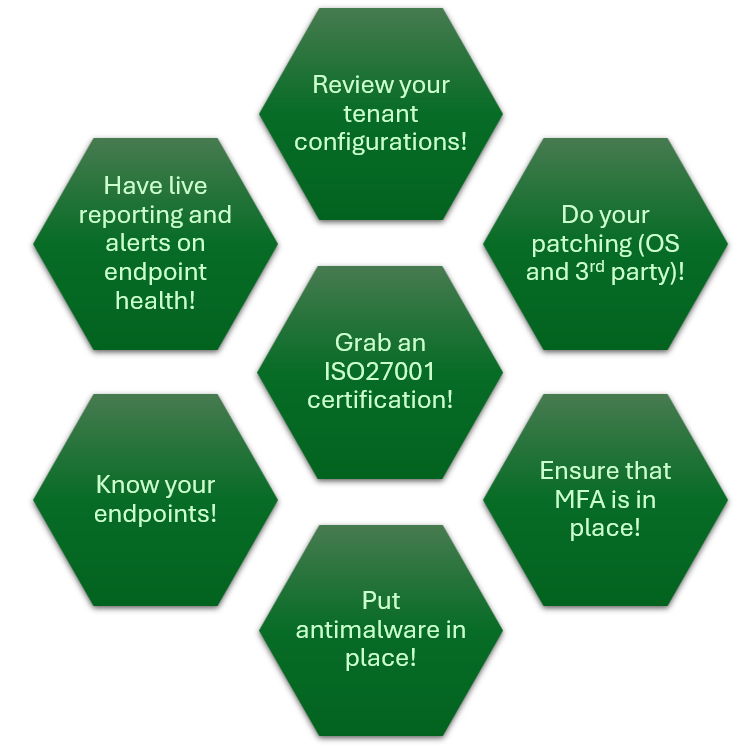
At the Very Least: Critical Controls for NIS2 Compliance
The following checklist comes straight from ISO 27001 and NIS2 requirements. If you’re offering endpoint management services, make sure these are covered across both internal and client environments:
- Multi-factor authentication (MFA)
- Encrypted devices: BitLocker, FileVault
- Regular updates and patching - not just OS, but 3rd-party apps too
- Compliance policies and Conditional Access
- Defender for Endpoint with real-time threat visibility
- Documented baselines and configuration policies
- Logging and audit trails for visibility and accountability
- RBAC and least privilege access for all admin operations
- Client-facing reports on endpoint health and compliance
- Incident handling and regulatory reporting (24h/72h timelines)
If you’ve got these controls in place - and can clearly communicate that to your clients - NIS2 compliance can become a competitive advantage rather than a bureaucratic burden. Many organizations are still trying to make sense of what’s required. If you’re already ahead of the curve, your ability to demonstrate readiness, reliability, and real visibility into endpoint security will set you apart in a crowded market.
Here’s the checklist of things you should consider verifying. You can also see how Plentics Suite could help you to tackle the issue.
| NIS2 focus area | What to do? | How does Plentics Suite help? |
|---|---|---|
| Multi-factor Authentication (MFA) | Enforce MFA for all privileged accounts and end users via Entra ID. Remove all permanent local admin rights. | Plentics provides analytics to ensure MFA policies are consistently applied. It allows temporary elevated access to eliminate permanent admin rights. |
| Device Encryption | Use Intune compliance policies to enforce full encryption on Windows, macOS, and mobile devices before access to corporate data. | Plentics surfaces encryption compliance data from Intune and enables centralized policy management, helping detect and fix non-encrypted devices. |
| Patching and Updates | Set up Windows Update for Business or Autopatch and implement 3rd-party patching tools. Monitor and automate update status. | Plentics consolidates update compliance data, automates 3rd-party patching, and alerts you about outdated systems across tenants. |
| Compliance & Conditional Access | Define compliance requirements (AV, OS version, encryption) in Intune and link to Conditional Access rules. | Plentics centralizes visibility of policies across tenants and supports policy documentation and bulk updates. |
| Antimalware & Threat Visibility | Onboard devices to Microsoft Defender or another AV. Enable automatic investigation and remediation of threats. | Plentics displays Defender protection and EDR status across tenants, improving awareness and helping prioritize response. |
| Security Baselines | Use Microsoft or custom baselines in Intune to apply consistent settings and document them for audits. | Plentics lets you create, replicate, and manage configuration profiles and policies across tenants, automating documentation. |
| Logging & Audit Trails | Enable logs in Intune, Azure AD, and M365. Route them to Sentinel or another SIEM for security event tracking. | Plentics automatically logs all actions and provides exportable audit trails that align with NIS2 compliance. |
| RBAC & Least Privilege | Use Intune RBAC and JIT access to restrict admin privileges based on roles. | Plentics includes built-in RBAC limiting team members to specific tenants and features per their roles. |
| Client Reporting | Generate reports from Intune or Power BI on compliance, device status, and risks for stakeholders. | Plentics automates report generation with client-ready content and allows alerts based on reporting data. |
| Incident Response & Regulation | Create a documented playbook with clear roles and regulatory timelines (24h/72h). | Plentics aggregates compliance/security data and supports fast detection, documentation, and regulatory reporting. |
What Should You Do Next?
If you're an MSP offering endpoint management, here are three practical steps:
- Assess your current state: Are your internal and client-facing practices aligned with NIS2?
- Implement at least items from the checklist above.
- Communicate clearly with clients: Help them understand how you’re making their environment safer and more compliant
Also, don’t overlook your own supply chain responsibilities under NIS2. By using ISO 27001 certified tools like Plentics and assessing your third-party dependencies, you strengthen not only your security posture but also that of your clients. And when it comes to client environments, help them establish basic user security awareness and make sure recovery processes are in place - because resilience isn’t just about prevention, it’s also about how fast you bounce back.
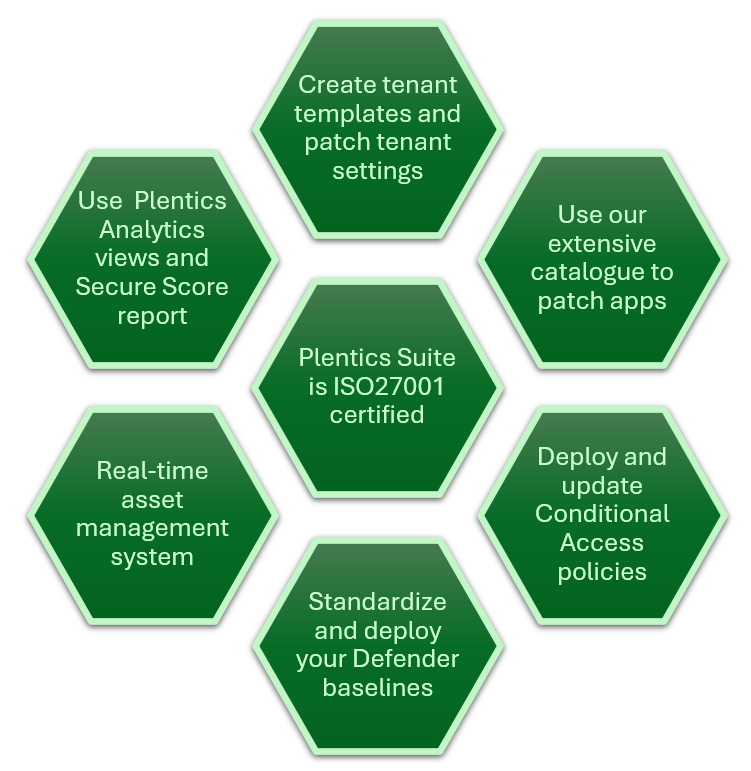
Plentics Suite is purpose-built to make Intune-based management easier across multiple tenants. Here’s how it helps:
- Automates policy rollouts and configuration replication.
- Makes multitenant management possible.
- Gives you a single pane of glass view of compliance across all clients.
- Makes it simple to generate client-facing reports and documentation.
- Bonus: Plentics is ISO 27001 certified - so using it strengthens your own compliance posture, including your supply chain responsibility.
Final Thoughts
NIS2 isn’t just another regulation - it’s a chance to upgrade your service and build trust. Solid endpoint management is at the heart of modern cyber hygiene. And with the right tools, it doesn’t have to be hard.
NIS2 compliance isn’t just about checking boxes, but about building trust, readiness, and resilience. If you’re already investing in strong endpoint management, don’t keep it a secret. Show it, share it, and turn it into a competitive strength.
Check out Plentics Suite and make sure both you and your clients gets all the benefits out of your NIS2-readiness in endpoint management.

Plentics is an ISO 27001:2022 certified company. We also have NIS2 compliance through Compleye's thorough verification process.






